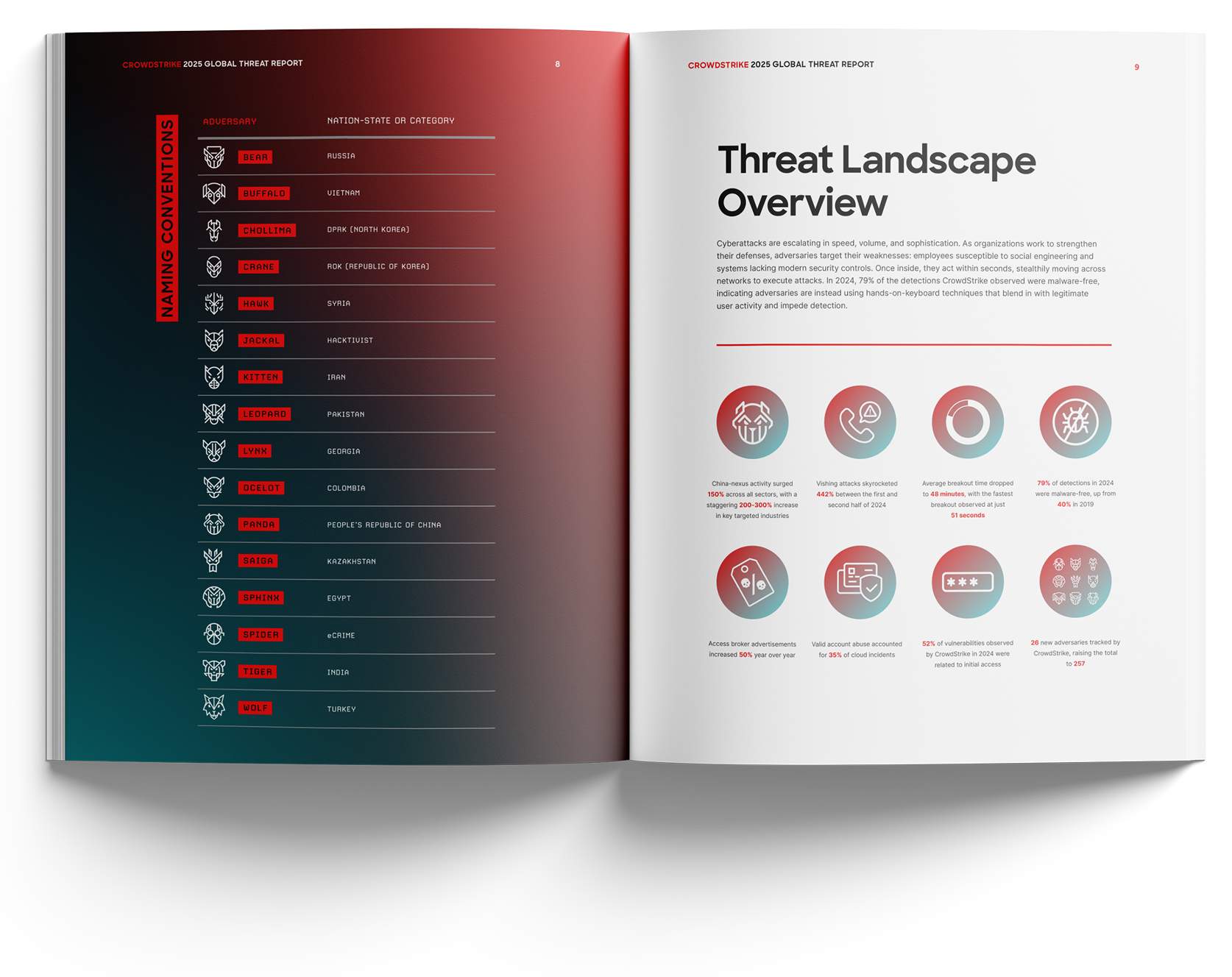
10 Mind-Blowing Cybersecurity Hacks That Will Shield Your Digital Life from Invisible Threats in 2024
In today's rapidly evolving digital landscape, protecting your online presence has become more crucial than ever. Let's dive into ten groundbreaking cybersecurity strategies that will help fortify your digital life against sophisticated threats in 2024 and beyond.

1. Zero-Trust Architecture Implementation
Gone are the days of implicit trust in your network. Embrace the "never trust, always verify" principle by implementing zero-trust architecture. This approach requires all users, whether inside or outside your organization's network, to be authenticated, authorized, and continuously validated before gaining access to applications and data.
2. AI-Powered Threat Detection
Leverage artificial intelligence and machine learning systems to identify and respond to threats in real-time. Modern AI-powered security tools can analyze patterns, detect anomalies, and respond to potential threats faster than traditional security measures.
3. Quantum-Ready Encryption
With quantum computing on the horizon, traditional encryption methods may become vulnerable. Start implementing quantum-resistant cryptography to ensure your data remains secure in the post-quantum era. This includes adopting the latest post-quantum cryptographic standards recommended by NIST.
4. Multi-Factor Biometric Authentication
Enhanced biometric authentication combines multiple biological identifiers like fingerprints, facial recognition, and voice patterns. This multi-layered approach significantly reduces the risk of unauthorized access and identity theft.
5. Automated Security Orchestration
Implement Security Orchestration, Automation, and Response (SOAR) platforms to streamline security operations. These systems can automatically detect, analyze, and respond to security incidents, reducing response time and human error.
6. Privacy-Preserving Computation
Utilize homomorphic encryption and secure enclaves to process sensitive data while maintaining privacy. This revolutionary approach allows computations on encrypted data without exposing the underlying information.

7. Blockchain-Based Identity Management
Implement decentralized identity solutions using blockchain technology. This approach gives users more control over their personal information while providing secure and verifiable digital identities.
8. IoT Security Mesh
Create a comprehensive security mesh around your IoT devices. This involves implementing micro-segmentation, continuous monitoring, and automated patch management for all connected devices in your network.
9. Cloud-Native Security Platforms
Adopt cloud-native security platforms that provide integrated protection across multiple cloud environments. These platforms offer unified security controls, automated compliance monitoring, and advanced threat detection for cloud-based assets.
10. Security Awareness Training 2.0
Invest in next-generation security awareness training that uses virtual reality and gamification. These immersive experiences help users better understand and respond to modern cyber threats through practical scenarios.
Best Practices for Implementation:
- Regularly update all software and systems
- Conduct periodic security audits
- Maintain encrypted backups
- Monitor dark web for potential data leaks
- Develop and test incident response plans
- Use password managers and generate complex passwords
- Enable automatic updates for security patches
The Road Ahead
As cyber threats continue to evolve, staying ahead of potential risks requires constant vigilance and adaptation. These ten cybersecurity measures provide a robust foundation for protecting your digital assets in 2024 and beyond. Remember, cybersecurity is not a one-time setup but an ongoing process that requires regular updates and improvements.
Ready to take your cybersecurity knowledge to the next level? Visit 01TEK to explore our comprehensive range of cybersecurity courses and resources. Our expert-led programs will help you master these advanced security techniques and prepare you for the challenges of tomorrow's digital landscape.
Sources: 1. CrowdStrike Global Threat Report 2. University of San Diego Cybersecurity Guide 3. DoD Cyber Exchange 4. Canadian Centre for Cyber Security 5. NIST Cybersecurity Framework 6. World Economic Forum Cybersecurity Outlook
Formal education will make you a living; self-education will make you a fortune.
Jim Rohn, author and speaker



