Zero-Day Nightmare: Hidden Vulnerability in Popular Software Puts Million of Systems at Risk
In today's interconnected digital landscape, cybersecurity threats continue to evolve at an alarming pace. A recently discovered zero-day vulnerability has sent shockwaves through the cybersecurity community, potentially affecting millions of systems worldwide. This critical security flaw demonstrates the ongoing challenges organizations face in protecting their digital assets.
Understanding the Threat
The zero-day vulnerability, tracked as CVE-2025-24984, has been identified in Microsoft Windows NTFS (New Technology File System), exposing critical information disclosure weaknesses. This previously unknown security flaw allows malicious actors to potentially gain unauthorized access to sensitive system information, putting both enterprise and personal systems at risk.
Widespread Impact
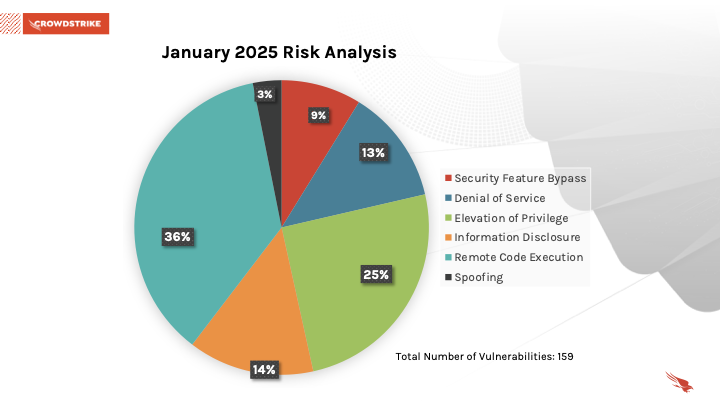
According to recent reports from CrowdStrike, the January 2025 Patch Tuesday release addressed a staggering 159 vulnerabilities, including eight zero-days and 10 critical vulnerabilities. This particular NTFS vulnerability stands out due to its potential for widespread exploitation across various Windows-based systems.
The Growing Threat Landscape
The cybersecurity landscape in 2025 has become increasingly complex, with AI-powered attacks and sophisticated exploitation techniques becoming more prevalent. Darktrace's cybersecurity predictions for 2025 highlight how emerging technologies and interconnected systems introduce new attack vectors and vulnerabilities that organizations must prepare for.
Real-World Implications
Recent incidents demonstrate the severe consequences of zero-day vulnerabilities. For instance, in January 2025, Fortinet firewalls were targeted through a new zero-day attack, showing how even security infrastructure can be compromised. The attack led to significant data leaks and highlighted the importance of rapid response to emerging threats.

Protective Measures
To protect against this and similar vulnerabilities, organizations and individuals should:
- Implement Immediate Patching: Apply the latest security updates as soon as they become available
- Conduct Regular Security Audits: Maintain comprehensive visibility of all systems and potential vulnerabilities
- Deploy Multi-Layer Security: Implement multiple security controls to create defense in depth
- Monitor System Activity: Use advanced threat detection tools to identify suspicious behavior
- Maintain Backup Systems: Ensure critical data is backed up and recoverable in case of compromise
Best Practices for Prevention
Organizations should adopt a proactive approach to cybersecurity:
- Regular vulnerability assessments and penetration testing
- Implementation of zero-trust security architecture
- Employee security awareness training
- Incident response plan development and testing
- Continuous monitoring and threat intelligence integration
Industry Response
The cybersecurity community has mobilized quickly to address this threat. Major software vendors have released emergency patches, while security researchers continue to analyze the vulnerability's full impact. The Cybersecurity and Infrastructure Security Agency (CISA) has added this vulnerability to their Known Exploited Vulnerabilities Catalog, emphasizing its critical nature.
Looking Forward
As we continue to navigate the evolving threat landscape, the discovery of this zero-day vulnerability serves as a stark reminder of the importance of robust cybersecurity practices. Organizations must remain vigilant and adapt their security strategies to address emerging threats effectively.
Take Action Today
Don't wait until it's too late to protect your systems. Update your software immediately, review your security protocols, and ensure your organization is prepared for emerging threats.
Ready to enhance your cybersecurity knowledge and skills? Visit 01TEK to explore our comprehensive range of cybersecurity courses and resources. Our expert-led training programs will help you stay ahead of evolving threats and protect your digital assets effectively. Join our community of security professionals and take the first step toward building a more secure digital future.
Sources: 1. CISA Known Exploited Vulnerabilities Catalog 2. CrowdStrike Patch Tuesday Analysis 3. Rapid7 Fortinet Zero-Day Analysis 4. Darktrace 2025 Cybersecurity Predictions 5. Apple Security Updates
A pessimist sees the difficulty in every opportunity; an optimist sees the opportunity in every difficulty.
Winston Churchill, British Prime Minister




